The Mechanics of Blockchain Hashes
Think of a ledger book, where each page contains a set amount of items, and all the pages are in order because they are connected by the book binding. This is exactly how a blockchain database functions, with each block containing a certain number of transactions, and each block bound to one another in numerical order.
Each transaction in the block contains several key pieces of data including:
- Where the transaction is originating from as well as its destination
- The value of the transaction and its gas fee (cost to send it)
- The type of transaction
- The transaction hash
All transactions and blocks are identified through hashes, which are the unique fingerprints for each transaction that never repeat.
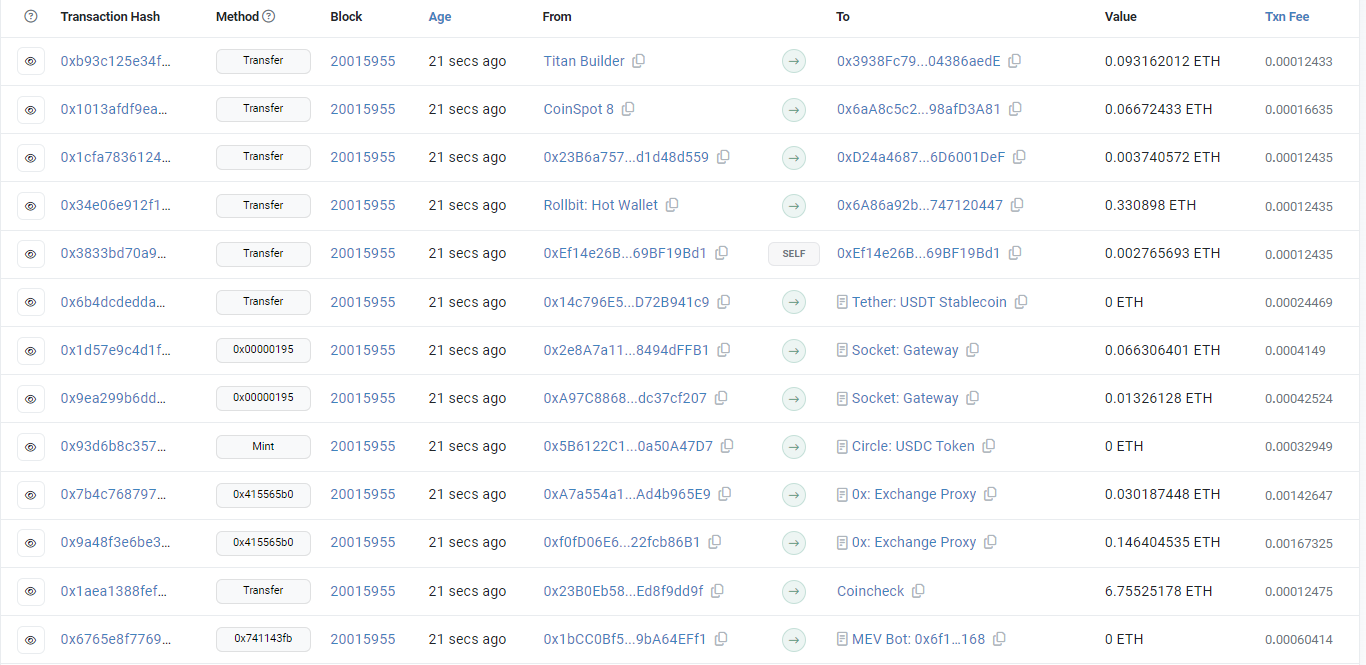
This image (to the right) contains a full list of actual transactions visible on-chain. Anyone can go and search for a transaction hash to identify any existing transaction that occurred using this system.
Source: Etherscan
Hashes work very well as identifiers because they have a property that makes them completely tamper-proof, which is that the output of a hash is directly based on the input it receives. The hash that is generated for any transaction is entirely based on the data that transaction contains; if any of the data changes, the hash changes as well.
💡 Creating a hash
To demonstrate how effective hashing is, let’s look at SHA-256, which is the encryption method that Bitcoin uses to create its hashes. If you take the string ‘pretend this is a Bitcoin transaction ’ and run it through a hash generator, it will return the following hash:
dafab953202ffc169d818e5cba59076848369712613357819fdb30f5b7ddac79
However, if you take that same exact string and add an exclamation point at the end and turn it into ‘pretend this is a Bitcoin transaction! ’, then the hash completely changes:
22d2db82e032157335c9d359d31ba11e11eff5d0019eed49d193abe08010c47f
If you remove the exclamation point, the hash returns to the original version.
Check out a hash simulator here to try this for yourself.
This type of data encryption makes your transactions tamper-proof. When a transaction is published onto the network and given a hash, that transaction can’t be altered, because then the hash would change and the data would no longer match.
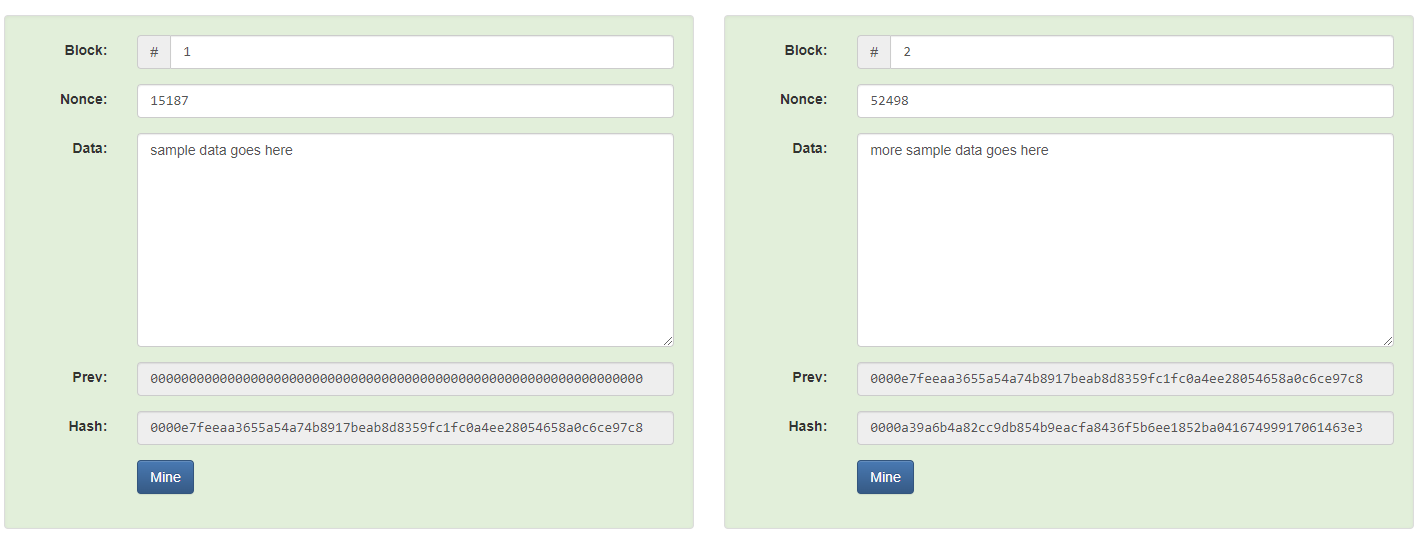
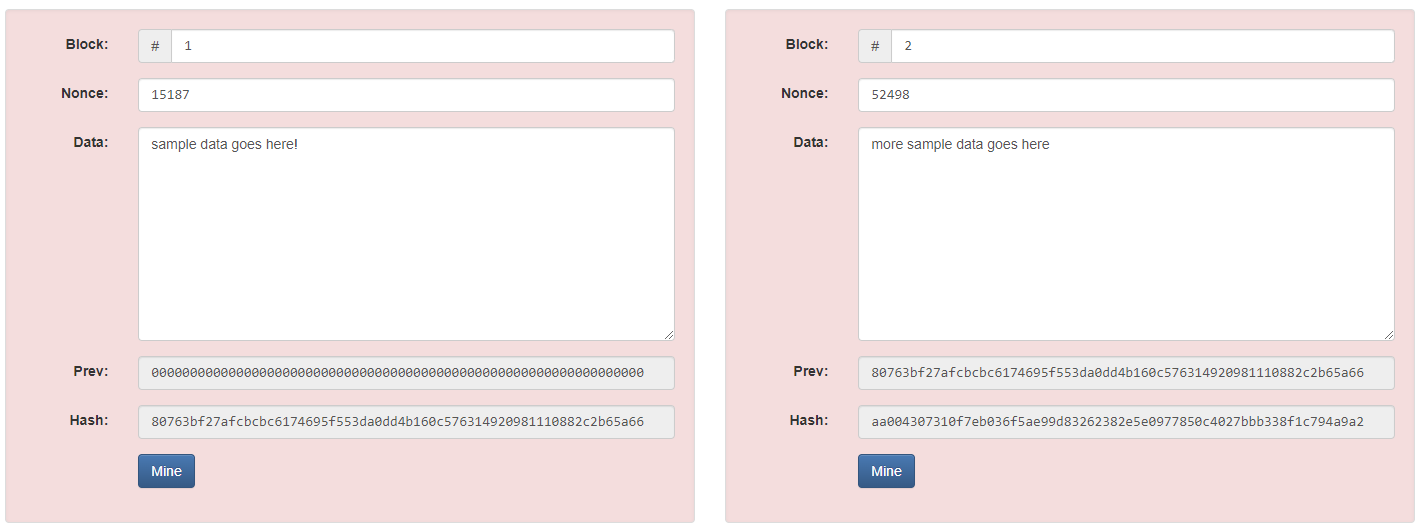
This principle is also applied to the blocks themselves, which have their own hashes. Each block contains its own hash that is generated by all of the transactions on it, as well as the hash of the previous block. This effectively creates the block chain, where each block is linked to the block before it to create an ordered system. This method also makes the blocks tamper-proof because a bad actor can’t edit a block without changing the hash. If they go to a previously published block and attempt to change its contents, the hash of the block will change, and the following blocks will become invalid because the hash that the next block has doesn’t match the new hash created.
Source: https://andersbrownworth.com/blockchain/blockchain
When two blocks are mined and then the first one is edited, its hash changes and the second block becomes invalid because the hash that it has for the first block no longer matches the actual hash of the previous block
Check out this website for an interactive demonstration of how this system works.
📋 Practice Question