Blockchain as a Tamper-Proof Network
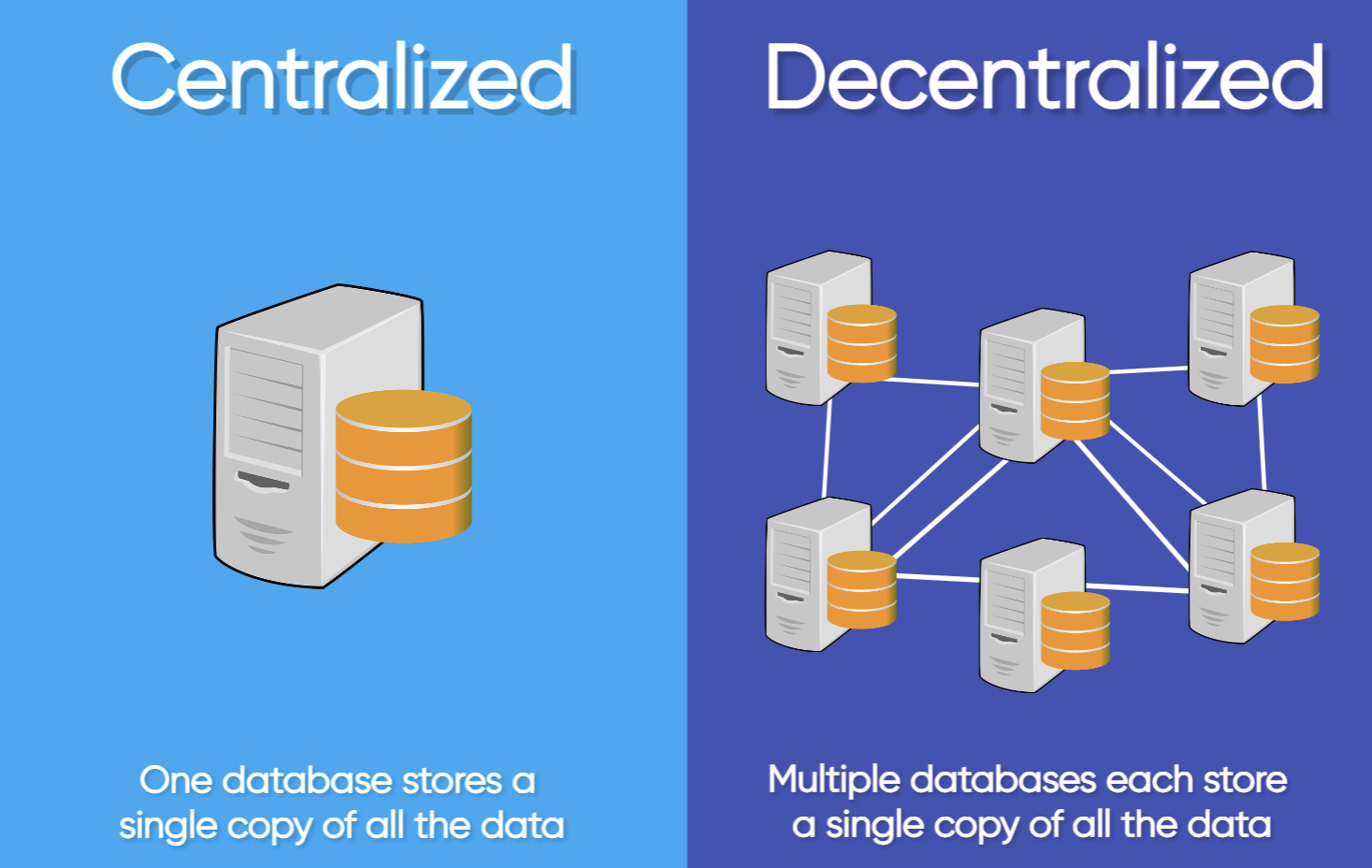
Blockchain works in a very unique way compared to traditional databases. Instead of storing data on one machine, a blockchain database operates across a whole network. Each node (a contributing computer) creates its own copy of the database and compares it to the results of the other nodes within the network. The correct state of the network is then reached once all the nodes agree on one version of the database.
While traditional centralized databases only hold one copy of all the data on them (not including backed up copies stored on the cloud), blockchain creates a system where each node on the network receives a copy of the data. For example, if there are 100 nodes operating a network, then there are 100 copies of the data, with each node receiving a copy. All of the nodes then have to come to an agreement on what is the correct version of the database by seeing which version is supported by the most nodes, where if 95 nodes have a matching version of the data while the other 5 have a slightly different version, the version backed by the majority of nodes becomes the accepted state of the blockchain.
The point of this process is to create a tamper-proof system that doesn’t let a database operator get away with making unsolicited changes to the network. In centralized databases, if a transaction is altered by the owner of that database or any other malicious entity, there would be no way to prove that the change wasn’t there before. On a blockchain network that contains copies of the database, if one node changes the database or gets hacked, all of the other nodes still have the unadulterated copy of the data and can prove that the affected dataset was manipulated.
Source: DCFT
💡 Transaction tampering example
Imagine you ordered a shipment of automobile parts. The company you ordered the parts from has a traditional centralized database where it tracks all orders. You need these parts delivered on the 20th to fix a vehicle, and you pay extra to receive priority shipping. There is a delay in the shipment, and instead of telling the company, the shipper changes the expected delivery date from the 20th to the 25th without informing them. You get angry at the company because the shipment was supposed to come on the 20th, but they check their centralized database and it shows the 25th, making it seem as if you are in the wrong.
If that company used a decentralized database, the fraudulent change would be noticed right away. The shipper would edit the transaction, which would be reflected on one of the nodes. However, when compared to the other nodes, it becomes evident that the manipulated node no longer matches, and the change would be detected.
In the case of Bitcoin, these nodes are the miners. When a miner is mining Bitcoin, they are actually a node contributing to the network by validating transactions and making their own copy of the database. They then get rewarded for their effort by receiving Bitcoin, which incentivizes them to keep mining and therefore operating the network.
While the nodes get paid to operate the network, regular users pay fees to create transactions. These fees are generally referred to as gas. Gas is paid for by the native currency of the given network, so in the case of the Bitcoin network, transactions are paid for using Bitcoin. The amount of gas required depends on the amount of congestion on the network; the more people using the network at a given time, the more transactions a miner has to process, the higher the gas.
Let’s break down the process of adding a new transaction to the Bitcoin network:
- You decide to send your friend some Bitcoin. You enter their wallet address, add an amount, and sign off on the transaction.
- Your transaction gets broadcast to the Bitcoin network and is received by the nodes operating the network. Once received by a node, the validity of the transaction is confirmed to be legitimate, and your transaction gets added into a list of transactions that need to be confirmed. This list is called a mempool.
- The node then selects the transactions listed in the mempool to include in the next batch of transactions. Each batch is called a block and all the blocks are all connected to one another, hence the name blockchain (a chain of blocks).
- The node then goes on to solve a complex cryptographic puzzle to get a number known as the nonce. The nonce, when combined with the data from the block, produces a unique identifier called a hash. This hash is very important because it serves as a fingerprint for each transaction that occurs on the network.
- Once the nonce is found, the new block that contains your transaction, among others, is created. The new block is then broadcasted to all of the nodes in the network, who confirm that it is valid and add it to their own copy of the blockchain.
- Once the new block is officially added to the network, your transaction receives a confirmation and the transaction is fully settled, and your friend use the Bitcoin you sent them.
Source: STEX
📋 Practice Question